Packet Capture
Packet sniffing of live traffic has become a common practice in Power Utilities since the deployment of IEC 61850 in order to analyse protocols such as GOOSE, SV, PTP and NTP
OKLAHOMA - JUNE 2022
Field Packet Capture
Improvements of storage technology in terms of capacity / speed and continuous optimization of Field-programmable Gate Array (FPGA) integrated circuits are bringing a totally new wave of possibilities in data capture and processing applications. Expensive and complex appliances based on Hard Disk Drive (HDD) arrays are not required any more. FPGAs are perfectly suited for wire-speed processing of fast data sources and small form factor Solid State Drives (SSD) supply excellent performance, large storage capacity and they are perfectly adapted to operation in portable equipment. One of the reasons of migration to SSD is that current cost of storage solutions based on flash memory allows to supersede past objections about price of these devices.
Wire-speed
Portable devices based on FPGA and SSD designs can be used in network troubleshooting, data forensics or security related applications when high capture speed and capacity is required but simple, reliable and fast configuration is important. Data capture is combined with the functionality of a network tap to enable easy access to the traffic stream that has to be analysed. Some applications, specially those related with security, require the capture device presence to remain unnoticed while it is connected to the network. Devices can be designed so that they do not modify the traffic information content or timing in any way even if they are connected in “bridged” mode allowing the traffic to be transmitted through the equipment.
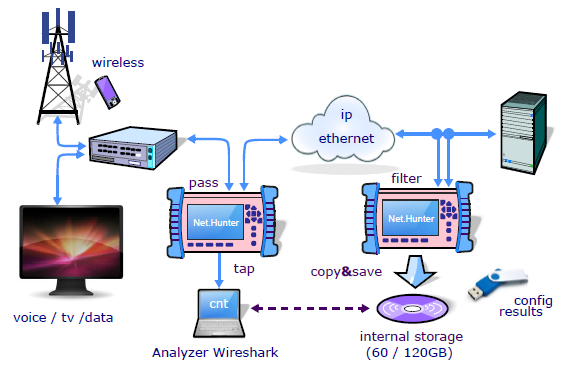
Fig 1. Net.Hunter a hand-held stream to disk appliance
Applications
Portable capture devices are ideal for enterprises looking to ensure that their networks are robust, scalable and secure. Applications of portable capture devices can be distributed in two large families: troubleshooting of communication networks and security. This is not a revolution when compared with traditional applications of any standard capture device. However, scenarios and applications of portable devices are considerably different and broader due to the ability to be connected and start operation in minutes without any special requirement. Portable capture devices are very well suited to temporary network connections in cases where analysis is required only for a limited period of time of usually a few hours or days.
- As result of the convergence process in the Power Utilities was released the IEC 61850 that defines a set of Ethernet-based protocols such as PTP, NTP, GOOSE and SV, to facilitate the interoperability between devices and manufacturers. When interconnection problems occur, it is essential to capture traffic in real time for later analysis and identification of responsibilities.
Fig 2. Substation automation often requires IEC 61850 protocol analysis
- Applications related with network troubleshooting include tracing of difficult to assess, temporary, intermittent problems. Traditional monitoring tools provide permanent information about the network in terms of various Key Performance Indicators (KPIs) but they are unable to deal with issues related with unexpected protocol interactions. Full protocol captures arise as the only way to deal with these problems.
- Portable capture devices are useful fighting against attacks like phishing linked to malware and other security threats. Event based pre-filtering could be used to detect intrusions. With the help of these tools, investigators will have the capability to reconstruct web sessions, e-mails and ‘chat line’ conversations in a chronological order to investigate security incidents.
- Finally, portable capture devices could be used in Lawful Interception (LI) applications. In case of portable devices the focus is again in non-permanent interception. Both filtering based on fixed patterns and event based filters could be used to built efficient LI based on wire-speed captures.
Advanced Capture Filters
Pre-filtering is an important feature even for devices prepared for wire-speed capture. With the help of filters, users make sure that only important data is going to be stored. For example, if only IP telephony signalling is going to be analysed, all other data can be ignored. The effect is a much better usage of the storage capacity. With the help of pre-filtering, it is possible to extend the maximum capture time from a few hours or minutes to days or weeks by constraining the raw volume of data. The second advantage of pre-filtering is that it can be used to mark packets depending on the filtering rule applied to match each of them. This classification can be used later for post-filtering and protocol analysis. Hardware processing is well suited to filter data based on fixed-length packet fields like IP / MAC addresses or class of service (CoS) marks (see Table 1). As a result it is possible to match any packet directed to an specific IP address, or directed to a network specified by its network prefix, or packets between two hosts specified by their source and destination addresses.
One Comment
Comments are closed.



Insightful! Your article on packet capture is informative and helpful for understanding network monitoring. Thanks for sharing this valuable knowledge!